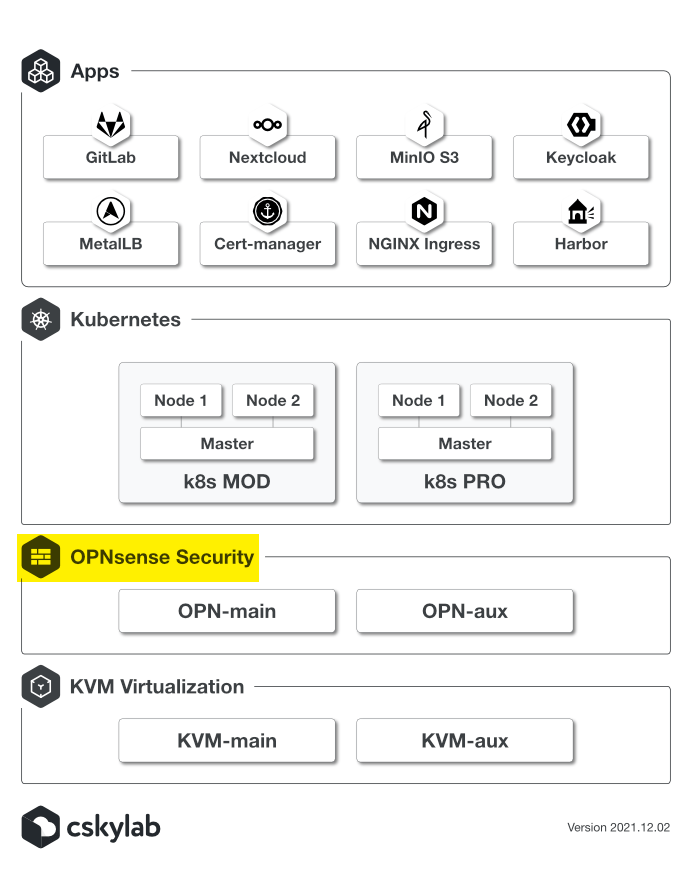
2 - OPNsense Security
Building OPNsense & mcc
This procedure explains how to build cSkyLab OPNsense security layer & management infrastructure
Configure OPNSense cluster
Restore configuration genesis
- Get DHCP assigned IP addresses to br_setup network for every machine. (You can connect to console via virt-manager in an Ubunto desktop VM)
- Connect to both machines GUI management interface:
https://<IPAddress>- Login with
rootNoFear21
- Login with
- Restore configuration genesis for
opn-mainandopn-auxon both machines respectively. - Reboot and check connection to both machines at
https://<IPAddress>:10443
Set secure specific configuration
This step updates initial configuration settings with specific security for your installation.
SECURITY WARNING: This step is mandatory to set a secured environment for your firewall and VPN access.
Prerequisites:
You must prepare the folder secrets in your repository with the specific information for your installation. (Private CA, passwords...)
Set root password
- Connect to
opn-mainandopn-auxmachines GUI consoles with https://IPAddress:10443 - Login with user
rootand passwordNoFear21 - Go to System -> Access -> Users. Edit
rootuser and change password. - Save configuration
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
Update synchronization password
- Go to System -> High Availability -> Settings and update
Remote System passwordwith the new password given. - Save configuration
- Go to System -> High Availability -> Status and check synchronization again by clicking button on
Synchronizeservice.
Set General Settings
In both machines opn-main and opn-aux configure general settings:
- Go to System -> Settings -> General
- Set Domain: Your installation name Ex.:
mpb-1100 - Save configuration
Virtual IP Settings
Note: You must have previously created in your internet uplink router the static IP Address for your OPNSense with a port forwarding rule for all protocols.
In opn-main configure virtual IP settings:
- Go to Interfaces -> Virtual IPs -> Settings
- Edit interface
WAN - Set Address to your WAN VIP address
- Set VHID Group to your assigned VHID group
- Apply changes to save configuration
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
WARNING: Both VIP address and VHID group must be unique among other OPNSense firewalls operating in the same WAN. The virtual MAC address of a CARP interface is
00:00:5e:00:01:XX, where the last two digits will be populated by its vhid.
- Go to Firewall -> Aliases
- Edit alias
WAN_VIP - Set Content to your WAN VIP address
- Apply changes to save configuration
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
Port Forwarding Settings
In opn-main configure port forwarding settings:
- Go to Firewall -> NAT -> Port Forward
- Edit rule in
Forward SSH to mccinWANinterface - Set Destination port range to your assigned port (Ex. 22-22 or another specific for your installation)
- Save configuration
- Apply changes to save configuration
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
WAN Rules
In opn-main configure WAN rules settings:
- Go to Firewall -> Rules -> WAN
- Edit rule in
Allow OpenVPN traffic from WAN - Set Destination port range to your assigned port range (Default is 49152-49156 for 5 VLAN's)
- Save configuration
- Apply changes to save configuration
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
Import private CA
- Go to System -> Trust -> Authorities and add a Certificate Authority
- In Descriptive name set the name of your CA
- In Method select
Import an existing Certificate Authority - Paste Certificate data and Certificate Private Key from your keys
- Save configuration
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
Generate VPN server certificate
You must create a certificate signed by your private CA
To create and sign a VPN server certificate go to System -> Trust -> Certificates and add a new certificate with the following settings:
- Method:
Create an internal Certificate - Descriptive name:
opn-cluster-VPN - Certificate authority:
Your private CA - Type:
Combined Client/Server Certificate - Key Type:
RSA - Key length (bits):
2048 - Digest Algorithm:
SHA256 - Lifetime (days):
3650 - Private key location:
Save on this firewall - Country Code: Your country code Ex.:
ES (Spain) - State or Province: Your State or Province Ex.:
Madrid - City: Your city Ex.:
Madrid - Organization: Your organization Ex.:
cSkyLab - Email Address: Your email address Ex.:
admin@cskylab.net - Common Name:
opn-cluster-VPN - Alternative names: Create wildcard SAN's for your domain (Or specific FQDN for the registered cluster DNS CNAME or address)
- Type:
DNSValue:opn-cluster-VPN - Type:
DNSValue:*.cskylab.net - Type:
DNSValue:*.cskylab.com(Used in FastStart hosted services)
- Type:
- Save configuration
Generate GUI server certificate (optional)
You can create a certificate signed by your private CA
To create and sign a VPN server certificate go to System -> Trust -> Certificates and add a new certificate with the following settings:
- Method:
Create an internal Certificate - Descriptive name:
opn-cluster-GUI - Certificate authority:
Your private CA - Type:
Server Certificate - Key Type:
RSA - Key length (bits):
2048 - Digest Algorithm:
SHA256 - Lifetime (days):
397 - Private key location:
Save on this firewall - Country Code: Your country code Ex.:
ES (Spain) - State or Province: Your State or Province Ex.:
Madrid - City: Your city Ex.:
Madrid - Organization: Your organization Ex.:
cSkyLab - Email Address: Your email address Ex.:
admin@cskylab.net - Common Name:
opn-cluster-GUI - Alternative names:
- Type:
DNSValue:opn-cluster-GUI - Type:
DNSValue:opn-main.cskylab.net - Type:
DNSValue:opn-aux.cskylab.net
- Type:
- Save configuration
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
Configure GUI certificate:
- Configure GUI Certificate from System -> Settings -> Administration
- Select SSL Certificate and choose
opn-cluster-GUI - Save configuration
- Select SSL Certificate and choose
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
OpenVPN Servers
Initial configuration comes with two preconfigured VPN servers:
mpb-genesis-mgtfor management accessmpb-genesis-usrfor general user access
To modify and secure VPN servers, connect to opn-main and configure the following settings:
Go to VPN -> OpenVPN -> SERVERS
Edit
mpb-genesis-mgtserver:- Set Description to Your installation name-mgt Ex.:
mpb-1100-mgt - Set Local Port to your assigned port for management vpn Ex.:
49152 - Set TLS Authentication to
Disabledto delete existing TLS Shared Key - Set Peer Certificate Authority to
Your private CA - Set Server Certificate to
opn-cluster-VPN - Save configuration
- Edit the configuration again and set TLS Authentication to
Enabled - Authentication only - Leave checked Automatically generate a shared TLS authentication key to generate a new TLS Shared Key.
- Save configuration
- Set Description to Your installation name-mgt Ex.:
Edit
mpb-genesis-usrserver:- Set Description to Your installation name-mgt Ex.:
mpb-1100-usr - Set Local Port to your assigned port for management vpn Ex.:
49153 - Set TLS Authentication to
Disabledto delete existing TLS Shared Key - Set Peer Certificate Authority to
Your private CA - Set Server Certificate to
opn-cluster-VPN - Save configuration
- Edit the configuration again and set TLS Authentication to
Enabled - Authentication only - Leave checked Automatically generate a shared TLS authentication key to generate a new TLS Shared Key.
- Save configuration
- Set Description to Your installation name-mgt Ex.:
Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
OpenVPN Users and certificates
Initial configuration comes with two preconfigured VPN users:
vpnmgt: Access to "management VPN"vpnusr: Access to "users VPN"
You can use directly these two generic users, or you can add personal users (and their specific access configuration files) if you want.
Set passwords for users
vpnmgtandvpnusr(Repeate these steps for each one):- Go to System -> Access -> Users
- Edit user
- Set Password and confirmation to your desired new password
- Save user configuration
- Go to System -> Access -> Tester
- Test Username and Password
Set User Certificate for users
vpnmgtandvpnusr(Repeate these steps for each one):- Go to System -> Access -> Users
- Edit user
- Delete previous User Certificate
- Add User Certificate with the following values (Leave the other values by default):
- Method:
Create an internal Certificate - Certificate authority:
Your private CA - Lifetime (days):
3650 - Private key location:
Save on this firewall - Country Code: Your country code Ex.:
ES (Spain) - State or Province: Your State or Province Ex.:
Madrid - City: Your city Ex.:
Madrid - Organization: Your organization Ex.:
cSkyLab - Email Address: Your email address Ex.:
admin@cskylab.net - Save certificate configuration
- Method:
- Save user configuration
Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
Export OpenVPN client profiles
You must export a profile for each user and server combination. Repeat the following steps for mgt and usr servers:
- Go to VPN -> OpenVPN -> Client Export
- In Remote Access Server Select your server (
mgtorusr) - Set Export type Choose
File Onlyfor OpenVPN Connect client orViscosity (visz)for Viscosity client. - Change Hostname to FQDN registered DNS CNAME or address (Ex.: Duck DNS registered name)
- Change Port to the apropriate server port (Ex.:
49152) - Check Use random local port
- Check Validate server subject
- Click the download button for the user profile to download.
- Save the downloaded profiles into your
opn-clusterconfiguration folder in your installation repository.
Note: You can send the downloaded profile file as an attachment, in an email message to the user. The user must import the profile with the client application (OpenVPN Connect or Viscosity) and test the connection from mobile and desktop environments.
Remove example certificates and ca-test-internal
- Go to System -> Trust -> Certificates and delete the following unused certificates:
| Certificate | Issuer |
|---|---|
| vpnmgt | ca-test-internal |
| vpnusr | ca-test-internal |
| OpenVPN | ca-test-internal |
- Go to System -> Trust -> Authorities and delete
ca-test-internalnot secure CA. - Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup.
Backup configurations and reboot
- Go to System -> High Availability -> Status and click button on
Synchronizeservice to synchronize config to backup. - Go to System -> Configuration -> Backups and backup configurations of both
opn-mainandopn-aux - Save the downloaded backup xml files into your
opn-clusterconfiguration folder in your installation repository. - Go to Power -> Reboot and reboot both
opn-mainandopn-aux
Test VPN's with vpnmgt and vpnusr profiles
- Import profiles to
OpenVPN Connectclient in your computer - Test connection to both VPN's
Configure mcc & VS Code Remote
Note: You must have pre-deployed in your computer your ssh keys.
- Connect to your lab in one of the following ways:
- Establish vpn session with
vpn_mgtprofile - Connect your computer directly to physical
sysnetwork in yourkvm-mainorkvm-auxmachines
- Establish vpn session with
- In your locally cloned subscription repository, open console in cs-sys -> mcc folder
- Check conectivity with
mcc:
- Check conectivity with
# mcc connectivitydig mcc.cskylab.netping mcc.cskylab.net
- Edit your
.ssh/configand add the following configuration lines to disable HostKeyChecking formcc:
# Disable HostKeyChecking for mccHost mcc.cskylab.netStrictHostKeyChecking noUserKnownHostsFile=/dev/null
- Open console into installation repository
cs-sys/mccfolder - Perform installation procedures for the machine:
# Run csinject.sh in [ssh-sudoers] execution mode./csinject.sh -k# Run csinject.sh to inject & deploy configuration in [net-config] deploy mode./csinject.sh -qdm net-config# Run csinject.sh to inject & deploy configuration in [install] deploy mode./csinject.sh -qdm install
Note: Delete records in your
$HOME/.ssh/known_hostsfile if needed.
Configure VS Code Remote with mcc
- Edit your
.ssh/configand add the configuration host for your mcc. You must use the hostname and ports exposed to the internet.
Example:
# Configuration for mcc at lab mpb-1100.cskylab.comHost mpb-1100.cskylab.comHostName mpb-1100.cskylab.comUser kosPort 49160
- In VS Code go to Remote Explorer -> SSH Targets and establish connection to
mccby right-clicking the mouse and selecting Connect host in a new window - Open terminal window and check connection to the remote machine as
kos@mcc
Clone git repository into mcc
- Navigate in your computer browser to your git installation repository and copy the url for Clone with HTTPS
- In VS Code Remote window, open terminal console at your home folder in
mccmachine - Paste and execute the clone command in your home directory with:
# git clone repositorygit clone https://csgit.cskylab.com/SubscriptionName/RepoName/.git
- Set username: Your username
- Set password: Your password or token
- In VS Code Remote window, open repository folder and browse it
Install cskygen in mcc
- In VS Code Remote window, open terminal console at
cskygenfolder.
To build and install cskygen binary file in $GOPATH/bin, open a terminal in the cskygen directory, and execute:
# Set environment variablesexport REPO_DIR="$HOME/mpb-1100"#Inject private CA files in mcc and k8s nodesecho && echo "******** SOE - START of execution ********" && echo \&& cd ${REPO_DIR}/cskygen \&& go install . \&& cskygen --version \&& echo && echo "******** EOE - END of execution ********" && echo
License
Copyright © 2021 cSkyLab.com ™
Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.